Passwords and Hacking (Part 2)
 The first part of this series is here.
The first part of this series is here.
These programs require a password to access your personal password database, but it is only one password. You can make that password very complex, even to the point of being a whole phrase. For example, if you start with a simple password of “psswrd” (don’t ever use “psswrd” or “password” as your password), then expand it to a whole sentence
Access for this file is through ‘password’.
You have a tremendously more complex password. If you now do the following character replacements: ‘l’ => ‘1’, “o” => 0, and “a” => “@”; and capitalize double letters, you get the following:
AcceSS f0r this fi1e is thr0ugh ‘p@SSw0rd’.
This phrase is so much more complex than that original 6 character password. One site gives an estimate to “discover” the password “psswrd” at about 5 minutes. A 14 character password with mixed case, digits, and special characters is over 150 billion millenniums. It would not be worth the effort to crack the password. Even a short 8 character complex password takes over 200 years. This is longer than it would take to directly attempt to decrypt the file.
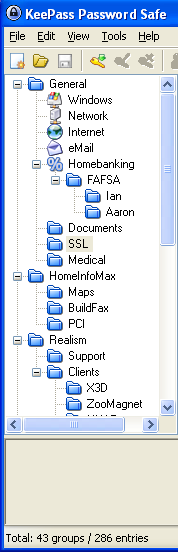
My personal favorite is KeePass (http://keepass.info). It is open source that runs on PC, Macintosh, and Linux. It allows you to keep your passwords organized in a hierarchical manner via a graphical display. It can be run from a thumb drive and does not leave any traces on the computer. The disadvantage of a thumb-drive operation is that you could loose or destroy it. If that is your only copy of your password database, then you have lost everything.
These programs are great if you only use one computer or can securely store the information on a local area network. They are not much help if you change computers frequently. This is especially true with smart phones. If you run a several different computers (between home, work, smart phones, and a traveling laptop), then you need a solution that is available from the Internet. An Internet-based solution (aka cloud-solution) has the same functionality as the desktop password managers, but runs from a web server.
Next time: Cloud-based password manager
